Subscribe to:
Comments
(
Atom
)
Popular
-
Explain Computer Mouse A computer mouse is a handheld hardware input device that controls a cursor in a G...
-
History of computer The history of computer starts from 4000 years ago. The gradual change in the co...
-
How to hack wifi on android devices Do you want to test your network security? Or you want to use the wifi of your neighbour and you do no...
-
Explain Keyboard A computer keyboard is one of the primary input devices used with a computer that looks ...
Comments
Categories
- Learn Basic Hacking (73)
- os (11)
- computer (10)
- windows 7 (9)
- how to tutorial (4)
- Access Jump Lists With The Left Mouse Button (1)
- Add clips from websites to Dashboard (1)
- Application based volume Mixer (1)
- Aug 2017 Updates Windows 8.1 Pro x64 ISO FREE Download (1)
- Backdoor Attack (1)
- Best time lapse app for android 2018 (1)
- Botnets (1)
- Brute Force Attack (1)
- Check Windows Version (1)
- Close In Attack (1)
- Control a mac remotely (1)
- Copy Command Prompt Output (1)
- Cross Site Scripting (1)
- DNS SERVERS (1)
- Defacing (1)
- Directory Traversal Loca (1)
- Distributed attack (1)
- Ethical Hacking Tutorial (1)
- Explain Backdoor (1)
- Explain Computer Mouse (1)
- Explain Internet (1)
- Explain Keyboard (1)
- Explain Microsoft (1)
- F and J keyboard keys bumps (1)
- Full Forms computer (1)
- How To Install Windows 7 Step By Step wi (1)
- How To Speed Up Any Internet Connection On Windows (1)
- How do I know if my computer has been hacked? (1)
- How t0 hack wireless networks (1)
- How to Download And Install IDM (Internet Download Manager) with CRACK Includ For Free (1)
- How to Install and Uninstall google chrome extension (1)
- How to access your pc from another pc (1)
- How to access your pc on android (1)
- How to boost and secure home WIFI (1)
- How to change your friends profile picture on whatsapp (1)
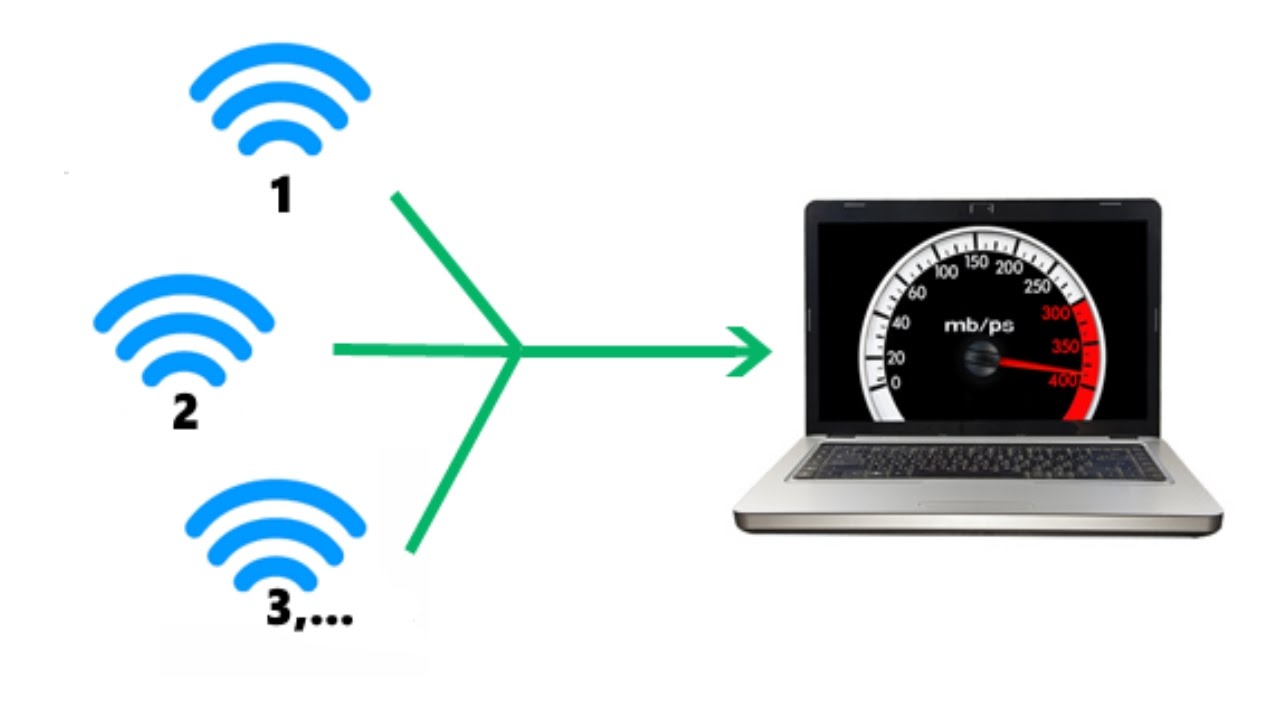
- How to combine two WIFI connection to get faster internet (1)
- How to create fake conversation on facebook and whatsapp (1)
- How to disable WIFI for others (1)
- How to disable applock in android (1)
- How to disable blue ticks on whatsapp (1)
- How to download Swift Stream Live TV on android (1)
- How to download all facebook account content (1)
- How to download paid apps for free (1)
- How to download torrent files from IDM (1)
- How to erase data so no one can recover (1)
- How to find IP address? (1)
- How to hack WIFI (1)
- How to hack a website (1)
- How to hack facebook account using phishing (1)
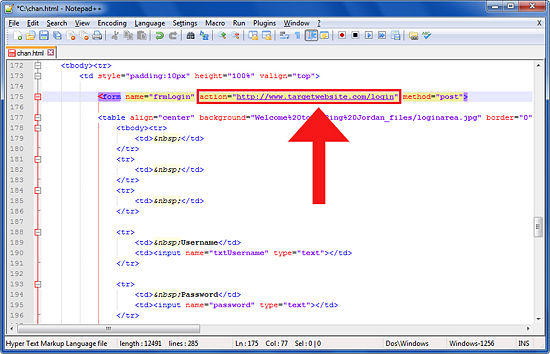
- How to hack website using html (1)
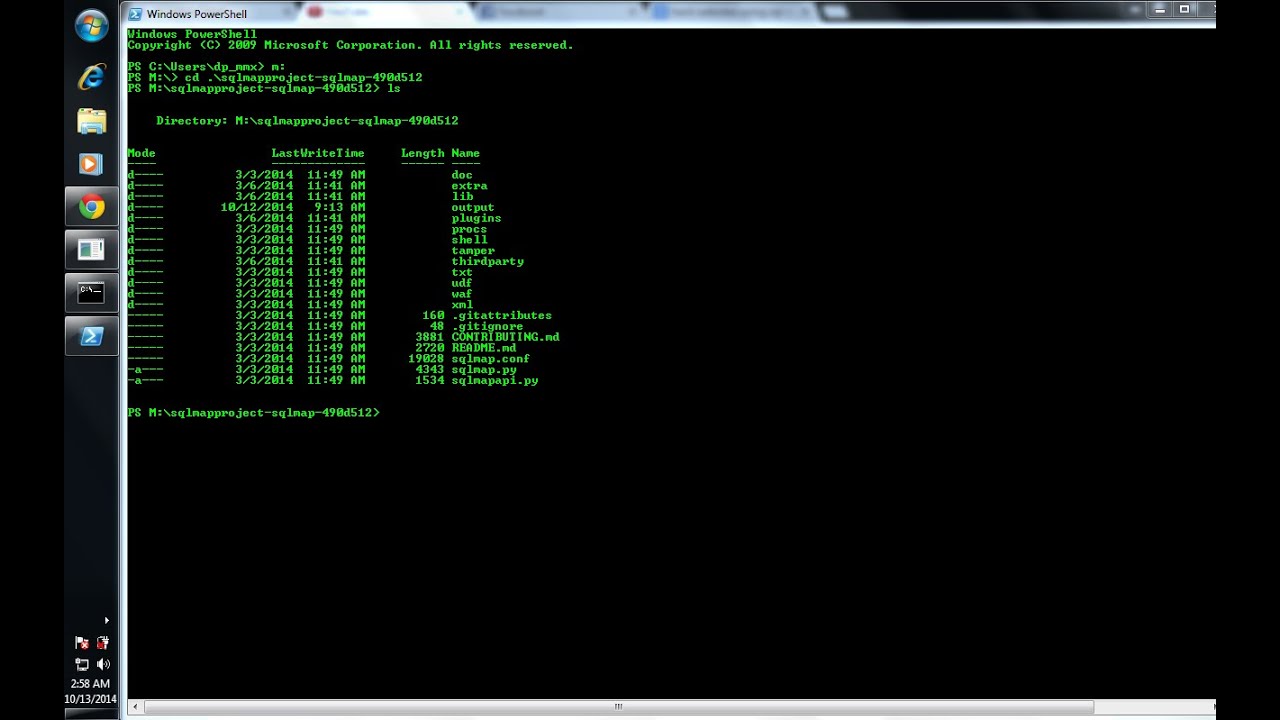
- How to hack website using sql injection (1)
- How to hack whatsapp account (1)
- How to hack wifi on android devices (1)
- How to hide your ip address (1)
- How to increase android phone performance (1)
- How to recover data from android phone (1)
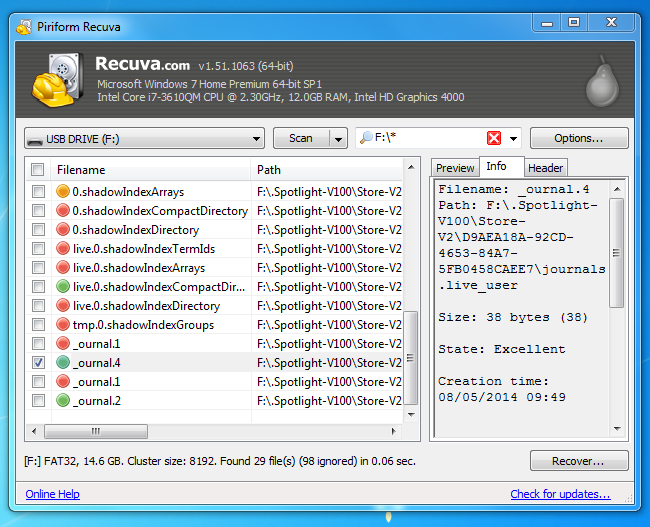
- How to recover deleted files from hard drive (1)
- How to recover facebook account after hack (1)
- How to recover whatsapp chat (1)
- How to remove shortcut arrow from desktop/laptop icon windows 7 8 8.1 10 (1)
- How to root android phone with pc (1)
- How to root your phone (1)
- How to secure facebook account (1)
- How to secure whatsapp account (1)
- How to send data from mobile to laptop (1)
- How to spy on someones whatsapp (1)
- How to stay Anonynomus online (1)
- How to track android phone (1)
- Insider attack (1)
- Junk Mail (1)
- Malware (1)
- Password attack (1)
- Ransomware (1)
- Remote File Inclusion (1)
- Run Windows (1)
- SPEED UP YOUR INTERNET (1)
- SQL Injection (1)
- Session Hijackinng (1)
- Snooping (1)
- Social Engineering (1)
- Start Menu (1)
- Talk to and listen to your mac! (1)
- Targeted Attack (1)
- Telephones facts (1)
- Trojan (1)
- WHAT IS PRIVATE BROWSING? (1)
- What Is My IP Address? (1)
- What is a Motherboard? (1)
- Why People Hack (1)
- WiFi eavesdropping (1)
- Windows 10 All in One (1)
- Windows 10 Enterprise ISO Download (1)
- Windows 7 All in One 32/64-Bit ISO free Download (1)
- Windows 7 Enterprise 32/64 Bit Free Download ISO (1)
- Windows 7 Home Basic 32/64 BIT Free Download ISO (1)
- Windows 7 Home Premium Free Download ISO 32 Bit 64 Bit os (1)
- Windows 7 Professional Free Download ISO 32/64 BIT (1)
- Windows 7 Starter Free Download ISO 32 Bit (1)
- Windows 7 Ultimate ISO Download 32/64 BIT (1)
- Windows 8.1 All in One ISO Free Download (1)
- Windows 8.1 Lite Edition 2018 OverVIew Free Download OS (1)
- Wondershare Video Converter Ultimate 10.2.0.154 Portable Download (1)
- Worms (1)
- Zero Day Exploits (1)
- case (1)
- keystroking (1)
- software (1)
- tips (1)
- virus (1)
- windows 7 Aero Blue Lite Edition (1)
- windows 8.1 (1)
- windows xp computer (1)
- windwos7 (1)
Blog Archive
- July 2018 (1)
- May 2018 (3)
- April 2018 (5)
- March 2018 (71)
- February 2018 (1)
- January 2018 (35)
Search This Blog
Contact Form
Popular Posts
-
How to hack wifi on android devices Do you want to test your network security? Or you want to use the wifi of your neighbour and you do no...
-
Explain Computer Mouse A computer mouse is a handheld hardware input device that controls a cursor in a G...
Created By Sora Templates & Blogger Templates
All Technology @ Tips And Triks 2018. Theme images by enot-poloskun. Powered by Blogger.